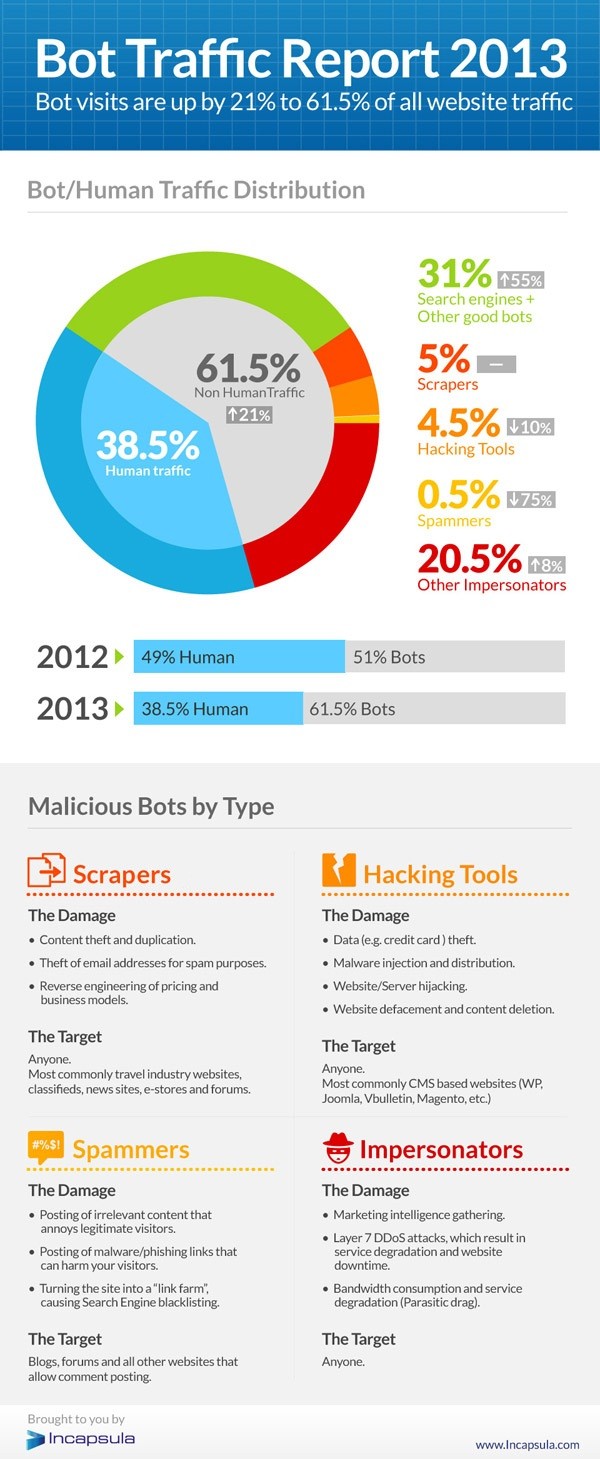
Beware of Marketplace Apps on the Move

Last week, Google announced that the Google Apps Marketplace was open for business to all Google Apps users, not just administrators.
While this move opens up a wide range of personal productivity applications to Google Apps users, it is not without risks.
- Your users can now commit you to paid apps and services that you may not want as part of your environment.
- Apps may require permissions to data in your Google Apps environment that needs to be, or you want to be, private and secure.
- Not all apps are from well-known vendors.
As we have written in the past, third party apps can present a risk to your data and your business. And while Bring-Your-Own-App (BYOA) can be beneficial to staff efficiency and effectiveness, Google Apps administrators should careful and should understand the security health of the domain.
As such, consider turning off marketplace access to all users. (Customers with a support plan: Ask us and we will do this for you).
We also recommend that you consider a Google Apps Security Health Check (special offer through Sept 30th) to ensure that Marketplace, mobile, and other third party apps are not already posing a risk.
If your current Google Apps reseller is not providing guidance on best practices, security and other important issues, contact us. We would love to have you join us as a client.





 As you have probably heard, there is a Federal lawsuit against Google in California that accuses Google of mining student data for commercial purposes. We have received a few questions and should expect we will have more.
As you have probably heard, there is a Federal lawsuit against Google in California that accuses Google of mining student data for commercial purposes. We have received a few questions and should expect we will have more.
