The Cloud, Shared Responsibility, and You
The vast majority of small and midsize businesses (SMBs) understand — or have learned the hard way — that the ability to recover lost or damaged data is critical to your IT services and business resiliency. You need to be able to recover and restore files, databases, servers, and workstations from loss due to disasters, hardware failures, software errors, or human action. In the cloud, it is your shared responsibility to protect your data.
The Cloud
As we move data, services, and servers, we rely on infrastructure and security built into the services. Google and Microsoft operate industry-leading, sophisticated services designed for security as well as performance, features, and functions. The capabilities do three things:
- Continuity: Ensure the clouds run with little or no disruption
- Recovery: Enable the restoration of services without loss of failure do to hardware, network, or other issues
- Capability: Provide us with the ability to secure and protect our data based on our usage
Microsoft, Google, and other cloud services do not, however, protect us from how we use their services.
You
Microsoft and Google do not control how we use Microsoft 365 or Google Workspace services. We, as subscribers, control how we manage and protect our data, including:
- Who can access the services
- Which applications can connect and integrate
- Which other applications and services will share user identities
- Which users can manage, edit, suggest, or view files and folders
- Which users can access various services within each of the productivity suites
With these controls comes great responsibility. You are responsible for how your data is stored and used. You are responsible if that use causes data loss or damage.
Shared Responsibility
Microsoft and Google both use a “Shared Responsibility” model for security and data protection. The model defines which aspects of the cloud service security and data protection are your responsibility and which are the responsibility of the service provider.
Microsoft
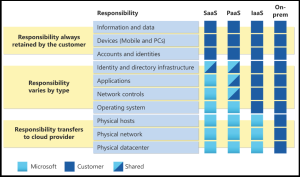 Microsoft discusses Shared Responsibility as a component of its terms of service. A recent Microsoft Learning article notes the following:
Microsoft discusses Shared Responsibility as a component of its terms of service. A recent Microsoft Learning article notes the following:
“In an on-premises datacenter, you own the whole stack. As you move to the cloud some responsibilities transfer to Microsoft. The following diagram illustrates the areas of responsibility between you and Microsoft, according to the type of deployment of your stack.”
For Microsoft 365, a “Software as a Service” (SaaS) offering, Microsoft expects you to take responsibility for protecting and recovery of your information and data; devices; accounts and identities; and portions of your identity and directory infrastructure. Microsoft has a detailed white paper covering shared responsibility for Azure services.
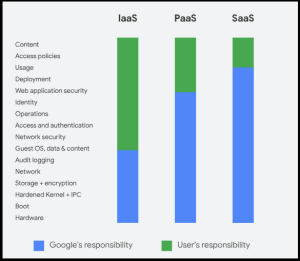 The Google Workspace Data Protection Guide includes a section dedicated to the Shared Responsibility model. Google states:
The Google Workspace Data Protection Guide includes a section dedicated to the Shared Responsibility model. Google states:
“Data protection is not only the responsibility of the business using Google Workspace services; nor is it only that of Google in providing those services. Data protection on the cloud is instead a shared responsibility; a collaboration between the customer and the Cloud service provider (CSP).”
“As a Google Workspace customer, you are responsible for the security of components that you provide or control, such as the content you put in Google Workspace services, and establishing access control for your users.”
As a SaaS offering, Google warns that you are responsible for the access control, security, and protection of any and all content you place in the Google Workspace service. The Google Cloud Platform: Shared Responsibility Matrix provides a detailed overview of shared responsibility for Google Cloud Platform.
Back to You
Understanding your shared responsibility, you can meet your data security and protection obligations.
First and foremost, configure and use the security and data protection features included within your Microsoft 365 or Google Workspace subscription. These services range from multi-factor authentication to secure user identities and access to advanced data loss prevention services in enterprise level subscriptions.
Your next step is to add additional services to cover aspects of data protection not provided with your Microsoft 365 or Google Workspace subscriptions. These services may include:
- Advanced threat protection for inbound email
- Backup/recovery of all user content in Google Workspace (including shared drives) and Microsoft 365 (including Teams)
- Archive/eDiscovery services to meet internal data policy, industry guidelines, or regulatory requirements
- Backup/recovery for data located on end user devices and on-premise or hosted servers
- Continuity services for mission-critical servers and end user device
- Message-level and file-level encryption for compliance with industry or regulatory requirements
Your business may or may not need all of the services listed. Which services you deploy should be part of a larger assessment of your cyber security and data protection needs.
Call To Action
Contact us or schedule time with one of our Cloud Advisors to discuss how you are meeting your shared responsibility and/or your broader security needs, priorities, and solutions.
For a broader look at your cyber security, complete our Rapid Security Assessment (free through June 2023) for a review of your basic security measures.
About the Author
 Christopher Caldwell is the COO and a co-founder of Cumulus Global. Chris is a successful Information Services executive with 40 years experience in information services operations, application development, management, and leadership. His expertise includes corporate information technology and service management; program and project management; strategic and project-specific business requirements analysis; system requirements analysis and specification; system, application, and database design; software engineering and development, data center management, network and systems administration, network and system security, and end-user technical support.
Christopher Caldwell is the COO and a co-founder of Cumulus Global. Chris is a successful Information Services executive with 40 years experience in information services operations, application development, management, and leadership. His expertise includes corporate information technology and service management; program and project management; strategic and project-specific business requirements analysis; system requirements analysis and specification; system, application, and database design; software engineering and development, data center management, network and systems administration, network and system security, and end-user technical support.

 What is a Third Party Data Breach?
What is a Third Party Data Breach? Allen Falcon is the co-founder and CEO of Cumulus Global. Allen co-founded Cumulus Global in 2006 to offer small businesses enterprise-grade email security and compliance using emerging cloud solutions. He has led the company’s growth into a managed cloud service provider with over 1,000 customers throughout North America. Starting his first business at age 12, Allen is a serial entrepreneur. He has launched strategic IT consulting, software, and service companies. An advocate for small and midsize businesses, Allen served on the board of the former Smaller Business Association of New England, local economic development committees, and industry advisory boards.
Allen Falcon is the co-founder and CEO of Cumulus Global. Allen co-founded Cumulus Global in 2006 to offer small businesses enterprise-grade email security and compliance using emerging cloud solutions. He has led the company’s growth into a managed cloud service provider with over 1,000 customers throughout North America. Starting his first business at age 12, Allen is a serial entrepreneur. He has launched strategic IT consulting, software, and service companies. An advocate for small and midsize businesses, Allen served on the board of the former Smaller Business Association of New England, local economic development committees, and industry advisory boards.
 On February 11, 2023, Google provided sixty (60) days notice of a Google Workspace fee increase across most licenses. For many customers, this increase is coming immediately after increased fees related to the transition from G Suite to Google Workspace.
On February 11, 2023, Google provided sixty (60) days notice of a Google Workspace fee increase across most licenses. For many customers, this increase is coming immediately after increased fees related to the transition from G Suite to Google Workspace.