Major Google for Education Licensing and Price Changes

As you are hopefully aware, Google announced major changes to both licensing and pricing for paid Google for Education editions.
These changes will impact most schools after February 1, 2026, and will affect some schools as soon as October 1, 2025. Depending on your annual renewal date, your district may experience a significant increase in Fiscal 2026 over current budgeted amounts.
The following are the licensing changes, pricing changes, and timing for the changes. We are also sharing our general recommendations based on your current subscription and plan.
Licensing Changes
- Google is eliminating licensing that differentiates between students (full and part time) and faculty/staff.
- All users will require the same license(s)
- You will no longer receive a staff license at no cost for every four (4) student licenses.
- Every active user must be assigned an Education Fundamentals license
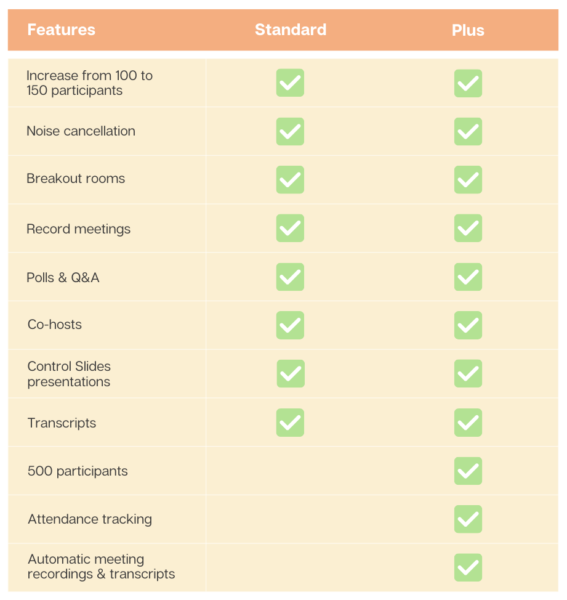
- Education Standard and Education Plus subscriptions are designed and intended to cover all active users, not just a subset.
- Partial domain licensing is no longer possible, with few exceptions.
- If you subscribe to either Standard or Plus, you must:
- Purchase enough paid licenses to cover every user with an Education Fundamentals license
- Ensure that all users with an Education Fundamentals license have an assigned paid license
- Google is enforcing a minimum purchase requirement for paid licenses of 50 seats.
- If your school has fewer than 50 faculty/staff and students, you must purchase 50 Education Standard or Education Plus licenses.
Pricing Changes
Google is increasing Google for Education pricing as follows. Note that subscriptions that were licensed and paid per-student will now be per-user, inclusive of students and faculty/staff.
Education Standard
- Price remains at $3 per user per year.
Education Plus
- Price increases from $5 to $6 per user per year
- If subscription cost increases more than 10%, you may be eligible for a 1-year 10% discount on your license fees
- Discounts are available with multi-year contracts
Teaching and Learning add-on
- Price increases from $48 to $60 per user per year for Annual/Fixed Term Plan Subscriptions
- Flexible Plan subscriptions increase from $4.80 to $6 per month
Timing of Changes
License and pricing changes start as early as October 1, 2025, for new all subscriptions and existing Flexible Plan subscriptions. The changes take effect beginning February 1, 2026, for all existing Annual/Fixed Term Plan subscriptions.
New Purchases
- For new Education Standard and Plus purchases, the new pricing takes effect as of October 1, 2025. The new pricing is for both Flexible (monthly) Plans and Annual/Fixed Term Plans (1+ year commitment with annual or monthly payments).
All Flexible Plan Subscriptions
- If you are on Flexible Plan (monthly) subscription, the new pricing begins as of October 1, 2025.
Annual Plan Subscription Renewals
- If you are on an Annual Plan Subscription, the price increase takes effect with your next annual renewal, on our after February 1, 2026. As such:
- If your renewal is before February 1, 2026, you may renew with the current licensing and pricing for one (1) year only. Any renewal for multiple years will use the new licensing structure and pricing.
- If your renewal is on or after February 1, 2026, your subscription will move to the new licensing and pricing structure upon renewal.
- Please note that
- If your renewal is after February 1, 2026 and within your current fiscal year, your new cost may not be fully budgeted if your budget was finalized before considering the new licensing and pricing structure.
- If you are renewing Education Plus and see a cost increase of more than 10%, Google will authorize a 10% discount for the first year of your renewal.
Annual Plan Subscription Upgrades
- If you are using Education Standard, you can upgrade to Education Plus using the current licensing structure and pricing until January 31, 2026. This includes mid-term upgrades that change your renewal date.
- As of February 1, 2026, upgrading from Education Standard to Plus will move you to the new licensing structure and pricing even if the upgrade is prior to your renewal date.
Downgrades
- If you choose to downgrade from Education Plus to the Teaching and Learning add-on, the new licensing and pricing takes effect October 1, 2025.
Our Recommendations
Depending on your current Google for Education subscription and plan, we recommend you consider the following:
New Education Standard and Education Plus Subscriptions
- Schools planning to add Education Standard or Education Plus should do so with an Annual Plan commitment before September 30, 2025.
- This will provide first year savings over the new licensing and pricing structure and provide you with the ability to properly budget for FY2027.
Current Education Plus Subscriptions
- Consider a multi-year commitment with possible discounts.
- Evaluate your usage and determine if downgrading to Education Fundamentals and using the Teaching and Learning add-on is appropriate.
Upgrading from Education Standard to Education Plus
- Schools planning this upgrade should do so with an Annual Plan commitment before September 30, 2025.
- This will postpone the price increase and will provide a year savings over the new licensing and pricing structure and provide you with the ability to properly budget for FY2027.
Flexible Plans
- Assess the stability of your user counts and, if feasible, move from your monthly plan to an Annual Plan prior to September 30, 2025.
- This will lock in current licensing and pricing for the first year and give you the opportunity to budget for increasing costs in the future.
We Will Help
Plan Now; Act Soon. As with any major change, we expect you will have questions and that you may need to reassess your budget. With the first deadline approaching October 1st, you have limited time to make decisions.
Our Cloud Advisors are here to assist. We can review your current subscription, discuss your options, and help secure the initial year and multi-year discounts.
Please schedule time with one of our Cloud Advisors for assistance.
About the Author
 Bill is a Senior Cloud Advisor responsible for helping small and midsize organizations with cloud forward solutions that meet their business needs, priorities, and budgets. Bill works with executives, leaders, and team members to understand workflows, identify strategic goals and tactical requirements, and design solutions and implementation phases. Having helped over 200 organizations successfully adopt cloud solutions, his expertise and working style ensure a comfortable experience effective change management.
Bill is a Senior Cloud Advisor responsible for helping small and midsize organizations with cloud forward solutions that meet their business needs, priorities, and budgets. Bill works with executives, leaders, and team members to understand workflows, identify strategic goals and tactical requirements, and design solutions and implementation phases. Having helped over 200 organizations successfully adopt cloud solutions, his expertise and working style ensure a comfortable experience effective change management.


 To state
To state 

 Allen Falcon is the co-founder and CEO of Cumulus Global. Allen co-founded Cumulus Global in 2006 to offer small businesses enterprise-grade email security and compliance using emerging cloud solutions. He has led the company’s growth into a managed cloud service provider with over 1,000 customers throughout North America.
Allen Falcon is the co-founder and CEO of Cumulus Global. Allen co-founded Cumulus Global in 2006 to offer small businesses enterprise-grade email security and compliance using emerging cloud solutions. He has led the company’s growth into a managed cloud service provider with over 1,000 customers throughout North America. You work with an IT service provider that learns your business, priorities, and IT needs. They work to address your needs and priorities within your budget and in alignment with your business goals and objectives. When economic conditions shift, the vendors with whom your IT service provider partners – Google, Microsoft, and others – get nervous and begin calling you directly, bypassing your trusted advisors.
You work with an IT service provider that learns your business, priorities, and IT needs. They work to address your needs and priorities within your budget and in alignment with your business goals and objectives. When economic conditions shift, the vendors with whom your IT service provider partners – Google, Microsoft, and others – get nervous and begin calling you directly, bypassing your trusted advisors.

 To meet widely varying customer needs, Google offers five core subscription options spread over two tiers. For larger organizations with frontline and deskless information workers, Google offers additional, specialized license options.
To meet widely varying customer needs, Google offers five core subscription options spread over two tiers. For larger organizations with frontline and deskless information workers, Google offers additional, specialized license options.