Changing the Focus on Backup Protection
As we’ve stated before, “Backup is easy; Recovery is hard”. Every business should, at this point, understand the risks of poor data backup and protection. The risks come from the types and amount of data that is lost and, if it can be recovered, how long that recovery takes. And remember, recovery often takes more effort than simply restoring files from a backup set.
Perspective = Priority
When looking at how well your backup system is protecting your business, two factors should be top of mind:
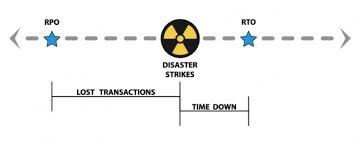
RTO: Recovery Time Objectives — How long will it take to return to normal operations. RTO is not just the time it takes to load your data back onto your systems, RTO includes the time it takes to repair and recreate damaged information and data created or modified since the last backup.
RPO: Restore Point Objectives — Your RPO determines how much data you are willing to lose, or can afford to lose. Most small and mid-size businesses backup daily. On average, a system failure will result in half a day of lost data. For an office worker editing a report, this is traumatic and inconvenient. For a manufacturer or retail business, half a day can represent hundreds or even thousands of orders and financial transactions.
As always, quicker RTOs and smaller RPOs come with trade-offs. Recovery methods like image snapshots, for example, can provide rapid RTOs and small RPOs. In exchange, you are likely losing granularity — the ability to recovery individual files.
Understand the reasons you are protecting your data. Protection from system failure, in which you need to recovery a full server, lends itself to imaging and other snapshot methods. Recovery of files or data lost to program error, malware, or user activity, needs a solution with granularity.
Start with an understanding of the type of protection you need and your RPOs and RTOs. From there, you can pick the solutions (yes, you may want or need more than one method) for recovering data and your business.
We offer a range data protection solutions, with a range of products, for on-premise and cloud-based data. Contact us for a free assessment of which type of solution is best for you.



