Posts
Not Using Google Drive? You Are Not Alone
/in Education, General![]()
CIO Magazine recently published a report claiming that 80% of Google for Work customers with more than 1,000 users are not utilizing Google Drive. The statistic is based on whether or not users worked with Drive at least once per month. This is disappointing given that studies show the powerful benefits realized when the collaborative features of Drive are fully utilized.
While the report does not discuss why Drive adoption is low, we have our suspicions.
Peer-to-peer file services do not scale — not without some help
In Drive (and oneDrive and other cloud file services), users create their own folders and share them with individual and teams. Each user “owns” their space and their files and to find a file, it helps to know who shared it with you. And, without central management, naming conventions, and other controls, it is difficult to control and manage access to sensitive information. While these file services are not as challenging as Windows for Workgroups (circa 1992), they come pretty darn close. Users familiar with a central file structure are easily frustrated with peer-to-peer sharing and file services.
“Security” is confused with “Sharing”
Yes, Google recently announced that Ernst & Young has verified the ISO 27018 cloud privacy standard for Google Drive. But when users think of security, they are concerned about sharing — or permissions — of their files. In any cloud file service, it can be difficult to fully understand who will have access to the file you are creating or uploading. And, the nuances of Google Drive can take time to learn.
For example, when sharing a link for a Google Doc with a person that does not currently have permissions, you are prompted to allow anybody with the link to view (or comment, or edit) the document. If your intended recipient forwards the message, access is available to others outside your original intention.
In Drive, and other similar services, the relationship between exposure (who can see, view, edit the file with or without credentials) and explicit access permissions has a learning curve that is often overlooked. People will avoid using Drive if they are worried about exposure and permissions.
The rules are a bit different
Google Drive is more flexible, and in many respects more powerful, than traditional Windows and Linux file shares. This power, however, can be distracting to end users. Having multiple documents with identical names in a folder, for example, throws many for a loop. It’s not intuitive given their experience and it can create confusion as to which document is correct or current.
Using Drive and other cloud file services is different, but you can take steps to ease the transition and improve adoption.
Train Your Users:
Beyond the basic “clicks and drags” of Google Drive, help your users learn and understand how to use Drive effectively. Cover permission settings so they understand how to share safely and with confidence. Discuss document naming and version management, including how to upload new versions of documents without creating duplicates. Help them learn now to navigate drive, use the search bar effectively, and launch applications from within the web interface.
Create a Managed File Service:
With an affordable add-on, you can overlay a more traditional file server structure onto Google Drive. Tools like AODocs File Server, you can add the aspects of a traditional file server to Drive:
- Central ownership and control of space, top level folders, and folder hierarchies
- Distributed access and permissions from a central authority
- Conversion of personal to central ownership of files uploaded to, or created, within centrally managed libraries
- Inherited permissions
- Audit trails
Yes, there is a cost, but the value for many companies is much greater.
Manage Your Permissions:
Permissions are not just about user settings. Permissions should — and can — be driven by your privacy needs and the content of your documents. Tools like BetterCloud and CloudLock give you the ability to monitor and manage user access and permissions based on business rules and content as it is created or uploaded. Analysis for HIPAA, PHI, PCI, and other compliance requirements is built-in, with the ability to create customized rules for your specific needs.
With the right tools, and a knowledgeable workforce, you and your team will better adopt and utilize Drive. And with adoption, comes results.
Please Contact Us if you would like information about any of the services mentioned in this post.
That Time Your Security Company Sold You Out
/in Education, General
As recently reported in Wired magazine, security firm AVG is updating its privacy policy and openly telling customers of its free services that it will sell some of the personal, non-identifying information about you to third parties. The new policy takes effect on October 15, 2015 and while the data may not identify you personally, it will certainly give advertisers, scammers, and hackers a clear idea of who you are and which of your interests they may be able to exploit.
As the policy states:
“We collect non-personal data to make money from our free offerings so we can keep them free, including:
- Advertising ID associated with your device
- Browsing and search history, including meta data
- Internet service provider or mobile network you use to connect to our products
- Information regarding other applications you may have on your device and how they are used.”
Granted, AVG gets credit for being upfront and honest.
But do you want your security software giving others your browser and search history, a list of applications on your devices, and a history of how you are using your apps?
The Advertising ID being shared means that so long as you have AVG on your device, third parties will know it is you even if they do not know specifically who you are (yet!).
Free is not free. Lesson Learned. AVG is telling you that in exchange for free security software, they will sell information about you to people that will use that information to advertisers, marketers, and those will try to scam you, steal your identity, and get you to bypass the very security you want to maintain.
Yes, you can upgrade to AVG’s paid services, but is this a company you still want to trust? Maybe it’s time for a new solution and a realization that even in IT, you get what you pay for.
If you prefer an endpoint security solution form a trusted vendor, contact us to discuss solutions or visit our web site for more information.
VDI Solutions: Uniting Performance, Scalability, and Cost-Efficiency
/in General
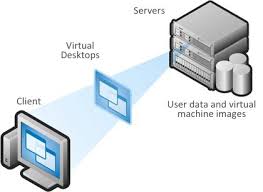 Like many organizations, your foray into cloud computing may have started with an ancillary or security service, like email spam and virus protection. For some, the first or second step into the cloud was moving email off-premise. For others, a cloud-based CRM service or VDI solution was the first application in the cloud.
Like many organizations, your foray into cloud computing may have started with an ancillary or security service, like email spam and virus protection. For some, the first or second step into the cloud was moving email off-premise. For others, a cloud-based CRM service or VDI solution was the first application in the cloud.
Currently, we see organizations rapidly moving file services and storage into cloud-based solutions as more marketing, sales, and line of business applications switch to Software-as-a-Service (“SaaS”) or SaaSOps solutions. Often, this leaves you with a small set of business applications running on-premise.
VDI Solutions Explained
What do you do with applications and services left on-premise when most of your systems have moved, or will be moving, to the cloud?
While you may wish to keep these legacy systems on-premise, you can move them into a cloud or hosted Virtual Desktop Infrastructure (VDI) environment. VDI environments provide a virtualized, remote desktop accessible via browser or “receiver” app. When connected, users get their full desktop environment with access to local and network applications.
Some applications, such as computer-aided design (CAD) and manufacturing/process controls, are not well-suited for VDI. Most local and network applications work well within a VDI environment. VDI services typically charge based on processor load, memory, and allocated disk space. Fees may also include standard office software, data backup services, malware protection, and other common network services.
Why use VDI Solutions?
- Improved secure accessibility to legacy applications, particularly for remote and mobile users
- Lower cost for IT and cloud infrastructure, especially when email, apps, and other services are moving to the cloud
- Improved reliability and security, as VDI solutions run in professionally managed data centers
- IT resources are free to work on higher value projects than maintaining core infrastructure and services
- Lower cost and less administration of end-user devices, as you can move to thin clients, chromebooks, and tablets as existing desktops and laptops need replacing
When to use a VDI Solution?
For some small and mid-size enterprises, VDI solutions provide a means to “clean out the closet”, to simplify their IT solutions and walk away from endless maintenance and updates. For others, a VDI solution enables them to move legacy systems and applications to a cloud-based environment.
When considering a VDI service for legacy applications and systems, answering a few basic questions while help you determine if your “when” is “now”.
- Is the application is available in a Software-as-a-Service (Saas) subscription?
- Does the application have custom modules or code that would prevent running the SaaS version?
- Are application requirements — processor power, memory, disk space — known and understood?
- How many users need access to the application?
- How many users receive reports or data from the application?
- What connections or integrations exist between local/network applications?
With answers to these questions, you can scope the size and configuration of your VDI environment. You can also assess if the benefits, and the costs, of a VDI solution outweigh the costs and effort required to maintain the systems on-premise.
As you move applications and services to the cloud, you will likely reach a point where you no longer have the critical mass necessary for on-premise servers to be the most economical and effective solution. When you reach this tipping point, a VDI solution will provide a secure home for your systems, your business, and your budget.
Our First eBook: 7 Policies for Every Company Using Drive
/in GeneralWe are please to announce the launch of our new eBook series with the publication of 7 Policies for Every Company Using Drive. Based on one of our most popular 3T@3 Webcasts, this eBook discusses information privacy and security issues and policies that should be in place to protect your customers, your information, and your business.
Our new eBook series is part of our growing suite of resources intended to help educate and inform on topics related to Cloud Computing for Small and Mid-Size Businesses.
Click here to access the eBook.
Cloud File Services: How to Define Their Role and Manage Data Better
/in Education, General
What Are Cloud File Services?
Users can store, access, and exchange files and data via online platforms known as cloud file services, also referred to as cloud file storage or cloud-based file sharing services. Without the use of physical storage devices or on-premise servers, these services offer a practical and effective solution to manage files from numerous devices and places.
Cloud file services can fill many different roles for your business. Often, the use of cloud file services begins with employees using consumer products, like Dropbox, to share files with customers and each other. While sync-and-share can be an effective way to manage files, you should always rely on the business editions to ensure that the business is in possession of, and is managing, your data.
That said, this use of file sync-and-share tends to be transient in nature. At the other end of the spectrum, many businesses are replacing on-premise servers, NAS, and SANs with cloud file services, which become the primary file service.
To help you plan how to create the best cloud file service for your business, consider these working definitions and considerations with respect to data protection and management.
Define the Role of Your Cloud File Service
Transient File Service
- Transient file services are used occasionally for storage and sharing of files.
- Often a sync-and-share service (Dropbox, box.net, etc) or a peer-to-peer service (Drive, etc.), files are copied to the file service and shared.
- In most cases, files sync back, or are manually copied, to their primary location. As the primary location for files is protected by backups and permissions management, transient file service generally don’t need or have backup protection.
- Permissions management is often the responsibility of the individual users. As such, transient file services should not be used for sensitive or protected (PHI, PCI, etc) information.
Secondary File Service
- A Secondary File Service will fill the role that the Transient File Service provides, but will also be the home — the system of record — for some information.
- Companies create Secondary File Services to handle information that is used collaboratively, but wants to keep internally-used data and critical business information in-house. An architecture firm, for example, might have active projects residing in a cloud file storage service while keeping past project data and internal operations (HR, finance, accounting, strategy) on in-house systems.
- While sync-and-share can serve the needs of secondary file server, peer-to-peer and managed file services provide better control over your data.
- As a Secondary File Service will be the system-of-record for important information (i.e., the data is not synced or copied to other storage), these file services should be protected by Backups.
- Secondary File Services may or may not be used for sensitive or protected information. If they are, then active permissions monitoring and management is advised to prevent inappropriate disclosures, leaks, or breaches.
Primary File Service
- A Primary File Service becomes the system of record for most, if not all, of your company’s files and data. As such, the cloud file service will hold sensitive and protected data. Access, permissions, and protection are as critical in the cloud as they are on-premise.
- Backup/recovery and active permissions management become critical components for ensuring data reliability, security, and privacy, and may be required for regulatory or industry compliance.
- While smaller businesses can use the peer-to-peer, larger businesses or those with larger numbers of files find that a managed and structured file service works better.
- Centralized ownership and control over permissions improves security and efficiency.
- Sync-and-share services may still be used to support off-line work, but should be managed closely to ensure sensitive and protected data remains secure.
Hybrid File Service
- A Hybrid File Service exists when the Primary File Service is split between on-premise servers and cloud-based file services. A Hybrid File Service differs from the use of a Secondary File Service in that the Hybrid File Service sees both on-premise and in-cloud as equal components of the ecosystem. Data location is based on access needs and usage rather than on the type of data.
- For some organizations, Hybrid File Services represent a transition period from on-site to cloud file services. For others, Hybrid File Services reflect a broader hybrid cloud strategy that mixes SaaS and IaaS services with on-premise systems.
- As Hybrid File Services create a cloud-based extension of on-premise servers, a managed file service with central ownership and permissions control is most often the best structure.
- With a Hybrid File Service, the cloud component requires backup/recovery and permissions protection on-par with your in-house servers.
By understanding and defining the role of your cloud file services, you have a better understanding of the type of managed cloud services to use — sync-and-share, peer-to-peer, or managed file services. You can also best determined the level of backup/recovery, access, permissions, and encryption you want and need to meet your business’ needs and any regulatory or industry requirements.
A Better Cloud Admin Solution
/in Education, General
With over 200 new features add yearly, the capability of Google Apps is growing in features and capabilities. Across our customer base, we see adoption and use of these features by individuals and teams growing as well.
You want and need to understand how Google Apps is being used, and working, for your business. With more collaboration and data in the cloud, you want to ensure that documents are properly shared, with appropriate privacy and protections. At the same time, we want to keep administration simple and efficient.
We have a solution:
BetterCloud recently release a new tiered service designed to solve each of these issues, and you can try it for free.
BetterCloud Basic is a Domain Health Center for your Google Apps domain, letting you monitor activity, define alerts, and analyze usage.
BetterCloud Pro is a robust suite of administration and management tools for Google Apps that simply admin tasks with an expanded set of controls that save you time and effort.
BetterCloud Enterprise adds auditing, discovery, compliance, and data loss prevention features, giving you the ability to monitor, manage, and mitigate data permissions and exposures in real time.
You can try BetterCloud for free, and without obligation. Here’s our offer:
We will …
- Install BetterCloud Basic for free in your Google Apps domain
- Activate a no-obligation, 30 day trial of the BetterCloud Enterprise and Pro Features
- Over the course of the free trial, we will highlight and demonstrate key features, including running a basic data security audit report for your review
At the end of the the trial, you decide if the cost/benefit of BetterCloud Pro or Enterprise is appropriate for your domain, and we will keep you subscribed. If not, you can keep using BetterCloud Basic for free.
To keep it simple, you can request the trial with two clicks. Click here* to open a request email, then click Send. Our team will promptly respond and activate your free trial.
*If you purchased Google Apps directly from Google, or another partner, we can still provide the trial. We also offer license discounts and other incentives for moving your account over to us. Contact us if you are interested in the savings and/or our services.
Reconsider Your File Sync-and-Share Services
/in Education, General
It is no wonder why file sync-and-share services are so popular. They are easy to setup and use, particularly with people outside your company or organization. And, most people you want to share with have, or are willing to create, a free account to see your shared files.
As a business, government, school, or non-profit, however, you may want to reconsider how you let your team use file sync-and-share services. Here’s why:
Who “Controls” the Data?
- Do you know if individuals are sharing information inappropriately?
- Could you recover files deleted by a user from their account?
File sync-and-share services create de facto peer-to-peer networks. Files are “owned” by the person that created or uploaded them. Permissions are controlled by each user, not by any central policy. As such, you have little ability to monitor or manage access to your data, which puts your business at risk for data breaches, as well as policy and regulatory violations.
Can You “Find” the File?
- Are you comfortable with a peer-to-peer file service with little central control?
- Are folks wasting time figuring out in which folder files are stored?
With each user creating folders and files to meet their own organizational needs, finding files shared with you can be challenging. As users create similarly named folders, locating files can be a challenge. You should never need to call a person for help locating a shared file.
Where, “Exactly”, is the File?
- Would a lost or stolen laptop or phone give somebody easy access locally saved files?
- Is locally saved data as secure as data on your server?
Chances are, your team is syncing files to/from laptops and mobile devices. So even if you are using a secure file sync-and-share service, your data is likely at risk. File sync-and-share services create local directories for storage and most services rely on your local security to protect those files. In other words, your data may be on a laptop or mobile device with no (or trivial) password protection. Adding drive-level encryption is an option, but adds money, complexity, and support costs to your environment.
Fortunately, solutions exist.
Secure, enterprise file sync-and-share solutions provide centralized control of what data can be synced to local devices, and by whom. These solutions also require login verification before accessing information on the local devices. Managed cloud file services let employees use locally installed apps with cloud-stored data, while providing centralized ownership and permissions management. Each solution has its limitations and benefits; understanding how your users need and prefer to work is key to making the picking the best solution.
Contact us for more information about available cloud file service options.
5 Reasons a Crypto Virus May Ruin Your Week
/in Education, GeneralMost businesses run some form of malware protection on their servers, desktops, and laptops. And yet, crypto viruses like cryptowall and cryptolocker still hit these “protected” networks.
Here are 5 reasons your virus protection may fail when it comes to crypto viruses:
1) Limited Virus Profiles
Most anti-virus systems run locally on each device. They compare file changes with patterns related to known viruses as a means of identifying malware. The pattern, or definition, database, however is typically only a few GB in size. With this limitation, it is impossible to detect the many variant forms for viruses.
2) Periodic Virus Updates
Most locally installed anti-virus systems update periodically by connecting to a local distribution server or the anti-virus software vendor’s servers. Because updates are not real-time, there can be a gap of hours or even days between when your system is unable to detect new viruses or variants.
3) Behavior Analysis
Chances are good that your anti-virus software has some intelligence or heuristics that identify behaviors as likely malware. Chances are equally good that this analysis is triggered by file actions. Few anti-virus solutions monitor systems for virus-like behavior (such as an application rapidly opening and closing files) that are not triggered by user action.
4) Quarantine instead of Rollback
Most anti-virus solutions quarantine files that have known viruses or are likely to be infected. With crypto viruses, however, quarantining the file with the virus does nothing to protect or recover the files that have already been encrypted.
5) Device-Specific
Most anti-virus solutions focus on PC and MAC platforms. But what happens when a virus is saved on a mobile device syncing with your server?
Fortunately, you do have options. Cloud based anti-virus solutions can overcome all five of these limitations. We offer a cloud-based solution that:
- Has a virus definition database over 2 TB (2,000 GB) in size
- Updates instantly and continuously when devices are connected to the Internet
- Analyzes behavior of the system and processes, not just those triggered by human action
- Will rollback suspicious activity, undoing damage before it can spread
- Has available protection across MAC, PC, Android, and iOS platforms from a single web-based console.
Here’s your Challenge
As a cloud-based solution with a minimal local footprint, we can install our service without interfering with your current anti-virus software.
Let us install a 30 free, no-obligation trial and see for yourself if your current anti-virus solution is giving you the protection you want or need.
To learn more about your options, or to request a trial, contact us today.
Best Ways to Protect Your Google Apps Account from Being Hacked
/in Education, GeneralWe have seen an alarming increase in the number of Google Apps accounts that have been “hacked” across both our business and education customers. Securing your Google Apps account is crucial to protect your sensitive information and prevent unauthorized access.
Google Apps platform security is NOT the issue. ALL of the hacked accounts are due to compromised user identities.
In every case we have encountered, the users have used their Google Apps email address and password with another service that has had a breach, or has had malware on their computer that provided username and password keystrokes to the hackers.
In both types of incidents, hackers then log in as the user and cause mayhem.
Essential Steps to Make Your Google Apps Account More Secure From Hackers:
1) Educate your users that they are not to use their Google Apps password for any other account not explicitly authorized. Users should also not use their Google Apps email address as the username for personal accounts with other services. It’s also critical to understand the risks of using third-party apps.
2) Check Your Systems for malware and make sure your endpoint protection is up to the task. If not, we recommend Webroot Endpoint Protection and Web Security Services (the link is to our edu site, but the service is available to business and government customers as well).
3) Implement Two-Factor Authentication (2FA). In business environments, users should be using 2FA to secure their accounts. Implementation can be involved if you have other services linked to Google Apps, as you will need to generate service-specific passwords.
4) Use Strong Passwords: Create a strong, unique password for your Google account. Avoid using easily guessable information and include a combination of upper and lower case letters, numbers, and special characters.
5) Review Account Activity: Periodically review the recent activity on your account. Google provides a “Last account activity” feature that allows you to check for any suspicious login attempts.
6) Check Account Permissions: Regularly review the apps and services that have access to your Google account. Remove access for any applications or devices that you no longer use or trust.
7) Beware of Phishing Attempts: Be cautious of phishing emails or websites that attempt to steal your login credentials. Always verify the authenticity of emails and URLs before entering your Google account information.
In education environments, 2FA is not practical for all users, as students and many faculty members may not have mobile devices available to access the Authenticator. For schools, we recommend any user with partial or full administrative privileges have 2FA active.
FAQs About Keeping Your Google Account Safe from Hackers
How do I secure my Google App?
Are Google accounts safe from hackers?
How does my Google Account keep getting hacked?
What is the best protection against having your Gmail account hacked?
Activating 2FA is covered by our support agreements.
For customers and others without support agreements, mention this blog post and we will discount our hourly support fee by 10%; W
We will discount Webroot deployment fees by 50%.
Both offers expire on December 31, 2014.
Please contact our Service Desk for 2FA assistance; contact Sales regarding Webroot.

Phone / Fax / Email
Headquarters / Boston
- Street Address
4 Bellows Rd / 2nd Floor
Westborough, MA 01581 - Mailing Address
PO Box 1129
Westborough, MA 01581-6129
Regional Offices
- Southeast Office
120 W Trinity Pl
Decatur, GA 30030
