What is Resiliency in Cloud Computing?
What is Resiliency in Cloud Computing?
In today’s rapidly evolving digital landscape, where businesses increasingly rely on cloud computing for their critical operations, the need to ensure uninterrupted services and data availability has become paramount. This is where “Cloud Resiliency” steps in as a fundamental aspect of modern IT strategy.
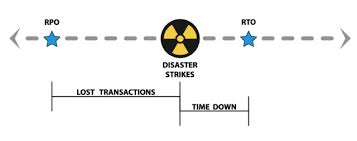
Cloud resiliency refers to the ability of a cloud-based system or infrastructure to withstand and recover from unexpected disruptions, whether they arise from hardware failures, software glitches, cyberattacks, natural disasters, or any other unforeseen events. It involves designing and implementing a robust framework that can promptly detect issues, gracefully handle failures, and swiftly restore normal operations without significant downtime.
The unexpected will happen. It is inevitable. Sometimes the unexpected is a good thing. In technology, the unexpected is usually bad. It may be small … or big … or catastrophic.
Part of our role as IT professionals is to expect and prepare for the unexpected. We backup data so that we can restore files that are accidentally deleted, overwritten, or damaged. We backup systems so that we can recover them in case of hardware or software failures. Many business designs and implement disaster recovery plans. These plans provide the means for companies to recover from larger incidents, ranging from burst pipes and building fires to blizzards and hurricanes.
In recent years, the focus has been on “Business Continuity” planning. Business continuity intends to prevent disruption to operations, even in the face of larger incidents or disasters. While great in concept, most small and mid-size enterprises cannot afford to fully duplicate systems in redundant data centers and provide alternate work sites for employees.
Cloud Resiliency in Business
Business Resiliency is based on the objective of enabling a business to continue (or rapidly resume) operations with some accommodations. In other words, you may not be running 100%, but you will be running soon enough and well enough, given the situation. Resiliency is about bending without breaking.
Consider Hurricane Sandy which devastated parts of the US Eastern Seaboard. Many businesses were physically destroyed by the flooding. Many others were shut down by the indirect effects of the flooding as some areas along the coast lost critical infrastructure — including water and sewer. Businesses left physically intact but without power for days considered themselves lucky as some areas waited months for reconstruction.
Consider the ice storms and blizzards throughout the Northeast US in recent years. For many businesses, the only disruption was loss of power. And while in many of the storms, outages where generally localized, some businesses went without power for as long as three weeks.
The same holds true for businesses in “tornado alley” in the Midwest. A tornado may leave your business unscathed, but it may take days or weeks for power and water to be restored.
In each of these scenarios, backup/restore/recovery is not enough to get the business back up and running. And, again, most small and mid-size businesses cannot afford to maintain disaster recovery systems and sites.
Benefits of Cloud Resiliency
Cloud resiliency offers a wide range of benefits to businesses and organizations that rely on managed cloud-based services and infrastructures. These advantages contribute to the overall stability, availability, and security of digital assets, ensuring uninterrupted operations and safeguarding against potential disruptions. Here are some key benefits of cloud resiliency:
- High Availability: Cloud resiliency ensures that critical applications and services remain available even in the face of hardware failures, software glitches, or other unforeseen events. Redundancy and failover mechanisms enable seamless transitions to backup systems, minimizing downtime and maintaining continuous access for users.
- Disaster Recovery: Resilient cloud architectures provide robust disaster recovery capabilities. Regular data backups, real-time data replication, and well-defined recovery processes allow businesses to recover quickly from data loss, cyberattacks, or natural disasters, minimizing potential data and revenue loss.
- Reduced Downtime: With cloud resiliency in place, businesses experience reduced downtime during system failures or maintenance activities. Quick detection and automatic recovery mechanisms help prevent prolonged service interruptions, enhancing productivity and customer satisfaction.
- Business Continuity: Cloud resiliency ensures business continuity by allowing organizations to maintain essential operations even during disruptive events. Critical business functions can continue operating, meeting customer commitments and minimizing financial losses.
- Cost Efficiency: While implementing cloud resiliency may involve upfront investments, it ultimately proves cost-effective in the long run. The ability to prevent extended downtime or data loss reduces potential revenue losses and protects a company’s reputation.
- Scalability: Resilient cloud infrastructures are designed to scale dynamically to meet changing demands. As businesses grow or experience fluctuating workloads, the cloud resiliency framework can seamlessly adapt, ensuring optimal performance and resource utilization.
- Enhanced Security: Cloud resiliency often goes hand-in-hand with robust security measures. Proactive identification and mitigation of vulnerabilities help protect against cyber threats and unauthorized access, safeguarding sensitive data and intellectual property.
- Improved Customer Trust: Reliability and continuous availability of services build trust with customers and partners. Knowing that their data and operations are in safe hands, clients are more likely to choose a resilient cloud service provider, giving businesses a competitive advantage.
- Regulatory Compliance: Resilient cloud architectures often adhere to industry-specific regulations and compliance requirements. Meeting these standards is critical for businesses operating in regulated sectors, ensuring legal adherence and avoiding potential penalties.
- Faster Recovery Times: In the event of a disruption or disaster, cloud resiliency enables faster recovery times compared to traditional on-premises solutions. Automated recovery processes and failover capabilities reduce the time required to restore services and operations.
- Geographical Redundancy: Resilient cloud infrastructures can be distributed across multiple data centers in different geographic locations. This geographical redundancy further enhances data protection and disaster recovery capabilities, minimizing the impact of regional outages or natural disasters.
Cloud Resiliency Requirements
Achieving cloud resiliency involves careful planning, robust architecture design, and the implementation of various measures to ensure the system can withstand and recover from unexpected disruptions.
Most businesses can afford to move IT systems into cloud computing and hosted solutions. And in doing so, businesses can affordably build resiliency.
With all of these disasters, you did not have to travel too far inland to be out of the damage zone. Businesses with on-premise equipment had to purchase and wait for delivery of replacements, rebuild their systems, and (hopefully) recover their data from their off-site backups. Certainly doable, but costly and time consuming. It can take 2 to 4 days just to get the equipment in place and ready to restore.
Businesses in the cloud faced a different scenario and outcome. Moving to an area with power and Internet, businesses running in the cloud were up and running in hours (some in minutes) and some were never “down” at all.
Take the Next Step Today to Implement Resilience in Your Cloud Computing Strategy
To discuss how cloud computing can improve the resiliency of your business, contact us for a no-obligation conversation or click here to learn about our RestartIT solutions.
![]() In our last blog post, we identified 3 must-have protections for any business using Google Workspace or Microsoft 365.
In our last blog post, we identified 3 must-have protections for any business using Google Workspace or Microsoft 365.
 Several weeks ago, in a town not far from our headquarters, a massive fire destroyed a building housing six small businesses. Our local business journal followed up a few weeks after the disaster with a poll asking business owners how prepared they are for a major disaster.
Several weeks ago, in a town not far from our headquarters, a massive fire destroyed a building housing six small businesses. Our local business journal followed up a few weeks after the disaster with a poll asking business owners how prepared they are for a major disaster. To paraphrase Newton’s Laws of Motion (with credit to Galileo) …
To paraphrase Newton’s Laws of Motion (with credit to Galileo) … A quick scan of the weather headlines late on Thursday afternoon: a “Nor’easter” storm going through rapid escalation, know as “Bombogenisis”, looks ready to hit New England tomorrow with rain, snow and hurricane force wind gusts. Now it is Sunday, and many small and midsize businesses along the northeastern coast are wondering when, or if, they will be able to reopen. The impact of disasters is increasing. We can argue about climate change versus weather. We can discuss our aging infrastructure. We can debate whether to plan for disaster causes or effects. If we do not, however, make our businesses more resilient, the quantity and severity of disruptions will continue to grow.
A quick scan of the weather headlines late on Thursday afternoon: a “Nor’easter” storm going through rapid escalation, know as “Bombogenisis”, looks ready to hit New England tomorrow with rain, snow and hurricane force wind gusts. Now it is Sunday, and many small and midsize businesses along the northeastern coast are wondering when, or if, they will be able to reopen. The impact of disasters is increasing. We can argue about climate change versus weather. We can discuss our aging infrastructure. We can debate whether to plan for disaster causes or effects. If we do not, however, make our businesses more resilient, the quantity and severity of disruptions will continue to grow. As reported in
As reported in 

 What is Resiliency in Cloud Computing?
What is Resiliency in Cloud Computing?