Security Best Practices to Protect Your Admin Accounts
 In any client environment, it is critical for you to protect your admin account with current security best practices. Most cloud services have multiple levels of admin accounts, including a super admin with the ability to access, manage, and change every configuration and security settings. In many cloud services, “super admin” accounts also have blanket access to your data. In effect your super admin and admin accounts hold the keys to your kingdom.
In any client environment, it is critical for you to protect your admin account with current security best practices. Most cloud services have multiple levels of admin accounts, including a super admin with the ability to access, manage, and change every configuration and security settings. In many cloud services, “super admin” accounts also have blanket access to your data. In effect your super admin and admin accounts hold the keys to your kingdom.
Protecting and managing admin accounts is critical for keeping your data and your business secure.
Here are four security best practices for managing and protecting admin accounts.
1 Multi-Factor Authentification
While we recommend multi-factor authentication (‘MFA”, also known as Two Factor Authentication or Two-Step Verification) for all user accounts, the added protection of MFA is critical for super admin and admin accounts. MFA helps to protect your admin account by preventing somebody from using stolen or compromised credentials to access your cloud services, your data, and your business.
For Super Admin accounts, consider a FIDO-compliant security key. These keys, or fobs, are physical devices that provide a timed access code required to log in. Keys provide the most secure method for multi-factor authentication, and are our number one recommendation when it comes to security best practices for administrator accounts.
2Secondary Super Admin Access
Even a super admin account can be lost or compromised. Should this happen, you need a way to perform critical admin tasks while you recover the super admin account. You have a few options, as follows.
- Create a second, dedicated, super admin account. While this comes with a licensing cost, you are not giving additional privileges to other admins or users.
- Assign super admin rights to an existing admin or user. You avoid any increased fees, but grant privileges which can be accidentally or intentionally misused. These privileges can include access to sensitive data, archives, and the ability to alter security settings.
- Engage your cloud partner/reseller. If your cloud partner/reseller has the ability to recover super admin accounts and/or reset super admin passwords, make sure you have a service or support agreement in place that covers admin account password reset and account recovery.
3Force Logout Super Admins
Day to day admin services can and should be performed by Admin accounts with permissions to perform specific sets of tasks. User your Super Admin account for specific administrative and security tasks not permissioned to other Admin accounts.
As a Super Admin: Log in. Perform the specific task. Log out.
If possible, set your system to automatically log out Super Admin accounts if idle for a short period of time.
4Privileged Access Management
Our final best practices to protect your admin account includes Privileged Access Management, or PAM, which limits access to critical security and administrative functions. Permission is granted to specific functions, upon request by another Admin or the system, for a limited amount of time. Using PAM provides additional tracking of who/when/why for critical settings and tasks.
Call To Action
Take a look at your cyber security. Complete our Rapid Security Assessment (free through June 2023) for a review of your basic security measures.
Contact us or schedule time with one of our Cloud Advisors to discuss your cyber security protections and/or your broader security needs, priorities, and solutions.
About the Author
 Christopher Caldwell is the COO and a co-founder of Cumulus Global. Chris is a successful Information Services executive with 40 years experience in information services operations, application development, management, and leadership. His expertise includes corporate information technology and service management; program and project management; strategic and project-specific business requirements analysis; system requirements analysis and specification; system, application, and database design; software engineering and development, data center management, network and systems administration, network and system security, and end-user technical support.
Christopher Caldwell is the COO and a co-founder of Cumulus Global. Chris is a successful Information Services executive with 40 years experience in information services operations, application development, management, and leadership. His expertise includes corporate information technology and service management; program and project management; strategic and project-specific business requirements analysis; system requirements analysis and specification; system, application, and database design; software engineering and development, data center management, network and systems administration, network and system security, and end-user technical support.

 Bill is a Senior Cloud Advisor responsible for helping small and midsize organizations with cloud forward solutions that meet their business needs, priorities, and budgets. Bill works with executives, leaders, and team members to understand workflows, identify strategic goals and tactical requirements, and design solutions and implementation phases. Having helped over 200 organizations successfully adopt cloud solutions, his expertise and working style ensure a comfortable experience effective change management.
Bill is a Senior Cloud Advisor responsible for helping small and midsize organizations with cloud forward solutions that meet their business needs, priorities, and budgets. Bill works with executives, leaders, and team members to understand workflows, identify strategic goals and tactical requirements, and design solutions and implementation phases. Having helped over 200 organizations successfully adopt cloud solutions, his expertise and working style ensure a comfortable experience effective change management.  Allen Falcon is the co-founder and CEO of Cumulus Global. Allen co-founded Cumulus Global in 2006 to offer small businesses enterprise-grade email security and compliance using emerging cloud solutions. He has led the company’s growth into a managed cloud service provider with over 1,000 customers throughout North America. Starting his first business at age 12, Allen is a serial entrepreneur. He has launched strategic IT consulting, software, and service companies. An advocate for small and midsize businesses, Allen served on the board of the former Smaller Business Association of New England, local economic development committees, and industry advisory boards.
Allen Falcon is the co-founder and CEO of Cumulus Global. Allen co-founded Cumulus Global in 2006 to offer small businesses enterprise-grade email security and compliance using emerging cloud solutions. He has led the company’s growth into a managed cloud service provider with over 1,000 customers throughout North America. Starting his first business at age 12, Allen is a serial entrepreneur. He has launched strategic IT consulting, software, and service companies. An advocate for small and midsize businesses, Allen served on the board of the former Smaller Business Association of New England, local economic development committees, and industry advisory boards.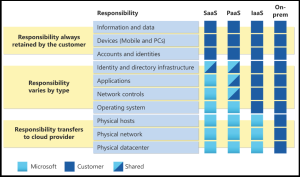 Microsoft discusses Shared Responsibility as a component of its terms of service. A recent Microsoft Learning
Microsoft discusses Shared Responsibility as a component of its terms of service. A recent Microsoft Learning 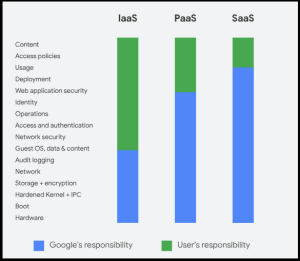 The
The  What is a Third Party Data Breach?
What is a Third Party Data Breach? To paraphrase Newton’s Laws of Motion (with credit to Galileo) …
To paraphrase Newton’s Laws of Motion (with credit to Galileo) …