Cloud Computing Trends, Challenges & Provider Insights in 2023
Cloud Computing Trends
Earlier this month, CRN published a story covering Flexera’s 2023 State of the Cloud Report. Flexera provides software and systems to manage enterprise private and public clouds. The report on cloud computing trends originates with an annual survey of 750 technology leaders across sectors, geographies, and size of the business. While the report classifies small and midsize businesses as those with under 1,000 employees, we still find the results interesting and relevant.
As small businesses, our concerns are spending, security, compliance, and managing cloud services. The cloud model hits our income statements and balance sheets differently than historical IT services. The need to protect our businesses, and our customers, has never been greater. And, we find it difficult to understand if we are spending efficiently and effectively.
We take a look at the top 3 cloud challenges, discuss managing clouds, and explore cloud waste. Understanding these issues, you will better understand how to create better cloud solutions. You will also be better able to set expectations from those providing cloud solutions and related services.
Top 3 Cloud Computing Challenges
For 2023, SMB respondents identify the top three cloud computing challenges as:
- Managing Cloud Spend (80%),
- Security (73%), and
- Compliance (71%).
These concerns make sense. The spending model for managed cloud services, based on subscriptions or usage, is an operating expense. Most smaller companies are used to making capital expenditures and paying for service contracts and managed services. Additionally, many of the IT firms working with small businesses will replicate on-premise networks and servers in a public cloud service. They may lack the expertise and tools to actively manage costs.
Concerns about security and compliance reflect the increasing need and demands of protecting sensitive business and personal information. We face the same increased regulations and expanding industry standards as larger enterprises. But we do not have the in-house resources or the same access to experts. We place our trust on local or regional IT service firms.
Latest Trends and Developments in Cloud Computing
Undefined Cloud Management
Following closely behind the top 3 cloud challenges, governance (67%) and subscription management (61%) indicate that small businesses are not sure how to best manage their cloud services. As cloud infrastructure matures, the number of options expand. To make simple decisions, such as whether to subscribe monthly or make an annual commitment at a lower per unit price, we need to understand the operating cost models. We need standard operating procedures, such as on/off-boarding and access controls, in place.
Cloud is still new. We need our IT service firms and managed service providers to guide, if not lead, our cloud management efforts. Co-management is a viable strategy, provided it includes policies and procedures as well as products and services.
Cloud Waste
On average, the survey results show that businesses spent 18% more than budgeted on public cloud services last year. The greatest contributor to the overspend appears to be Cloud Waste.
Cloud waste is spending on cloud services that go unutilized or are under-utilized. Reducing cloud waste can be as simple as
- Shutting down unused resources after hours
- Selecting lower cost regions / data centers
- Periodically right-sizing systems and resources
Policies that scale resources in real-time based on usage will increase efficiency, but require expertise and planning during the solution design process, monitoring, and refinement over time.
How to Pick a Cloud Computing Provider
Traditional managed service providers, or MSPs, are experts in buying, monitoring, and managing things. They focus on network components, servers, systems software, and end user devices. To get the most value from our cloud services, we need partners that understand service and cost management.
Managed cloud service providers, or MCSPs, understand how the “as-a-Service” model is different. Security, compliance, and cost management only work when they are built into the requirements, design, and management of your cloud services.
Before picking your cloud provider, ask about their management and co-management models. Understand if they actively work to monitor and manage security, compliance, and costs. Ask them to explain how.
Call To Action
Get a copy of our recent eBook, Cloud Strategies for Small and Midsize Businesses. In this eBook, we: set the stage by looking at how small and midsize businesses acquire and use technology and IT services; explore the challenges we face moving into the cloud; and map out four strategies for enhancing your use and expansion of cloud services.
To discuss how your business can better utilize a broader range of cloud services, please contact us or schedule time with one of our Cloud Advisors at your convenience.
About the Author
 Allen Falcon is the co-founder and CEO of Cumulus Global. Allen co-founded Cumulus Global in 2006 to offer small businesses enterprise-grade email security and compliance using emerging cloud solutions. He has led the company’s growth into a managed cloud service provider with over 1,000 customers throughout North America. Starting his first business at age 12, Allen is a serial entrepreneur. He has launched strategic IT consulting, software, and service companies. An advocate for small and midsize businesses, Allen served on the board of the former Smaller Business Association of New England, local economic development committees, and industry advisory boards.
Allen Falcon is the co-founder and CEO of Cumulus Global. Allen co-founded Cumulus Global in 2006 to offer small businesses enterprise-grade email security and compliance using emerging cloud solutions. He has led the company’s growth into a managed cloud service provider with over 1,000 customers throughout North America. Starting his first business at age 12, Allen is a serial entrepreneur. He has launched strategic IT consulting, software, and service companies. An advocate for small and midsize businesses, Allen served on the board of the former Smaller Business Association of New England, local economic development committees, and industry advisory boards.

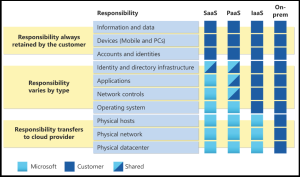 Microsoft discusses Shared Responsibility as a component of its terms of service. A recent Microsoft Learning
Microsoft discusses Shared Responsibility as a component of its terms of service. A recent Microsoft Learning 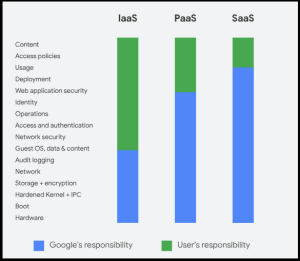 The
The  Christopher Caldwell is the COO and a co-founder of Cumulus Global. Chris is a successful Information Services executive with 40 years experience in information services operations, application development, management, and leadership. His expertise includes corporate information technology and service management; program and project management; strategic and project-specific business requirements analysis; system requirements analysis and specification; system, application, and database design; software engineering and development, data center management, network and systems administration, network and system security, and end-user technical support.
Christopher Caldwell is the COO and a co-founder of Cumulus Global. Chris is a successful Information Services executive with 40 years experience in information services operations, application development, management, and leadership. His expertise includes corporate information technology and service management; program and project management; strategic and project-specific business requirements analysis; system requirements analysis and specification; system, application, and database design; software engineering and development, data center management, network and systems administration, network and system security, and end-user technical support. The Impacts: Profits, Revenue, Cash, and Survivability
The Impacts: Profits, Revenue, Cash, and Survivability
 What is Resiliency in Cloud Computing?
What is Resiliency in Cloud Computing?