Inc. Names Cumulus Global to the 2025 Inc. Regionals Northeast List
 Companies on the Inc. Regionals: Northeast list added $6.7 billion to the Northeast US economy
Companies on the Inc. Regionals: Northeast list added $6.7 billion to the Northeast US economy
Westborough, MA – April 1, 2025 – Cumulus Global proudly announces Inc.’s recognition Cumulus Global at No. 152 on its 2025 Inc Regionals: Northeast list. The company’s inclusion on the fifth annual listing of the fastest growing private companies in the Northeast follows Cumulus Global’s prior recognition in the Inc. Power Partner and Inc. 500/5000 lists.
“We greatly appreciate the recognition of our continued growth and contribution to the regional economy,” noted Allen Falcon, CEO. “Our growth reflects the commitment of our team to deliver productive, secure, and affordable managed cloud services to small and midsize businesses, local governments, and K12 school systems.”
An extension of the national Inc. 5000 list, the Regionals offer a unique look at the most successful companies within the Northeast economy’s most dynamic segment–its independent small businesses.The companies on this list show a remarkable rate of growth across all industries in the Northeast. Between 2021 and 2023, these 154 private companies had a median growth rate of 100 percent; by 2023, they’d also added 9,114 jobs and $6.7 billion to the region’s economy.
“The honorees on this year’s Inc. Regionals list are true trailblazers driving economic growth in their respective regions, industries, and beyond. This list celebrates their achievements and tells the stories of remarkable companies that are fueling growth and adding jobs in local economies throughout the country,” said Bonny Ghosh, editorial director at Inc.
Complete results of the 2025 Inc Regionals: Northeast including company profiles, can be found at https://www.inc.com/regionals/northeast as of April 1. You can sort the list by by industry, metro area, and other criteria.
About Cumulus Global
Cumulus Global helps small and midsize organizations thrive and grow with productive, secure, and affordable managed cloud services.
- What We Do: We translate your business goals and objectives into solutions and services.
- How We Do It: We start with your business needs and priorities. Planning and migration includes guidance to help your team adopt and utilize new services. Your team benefits from co-managed services, on-going support, and client success services. We help you adapt as your business changes and grows.
- What We Offer: Managed cloud solutions featuring Google, Microsoft, and more than three dozen providers.
For more information, schedule a no-obligation introductory meeting with a Cloud Advisor.
More about Inc. and the Inc. Regionals
Inc., the leading media brand and playbook for the entrepreneurs and business leaders shaping our future, publishes the most prestigious ranking of the fastest-growing private companies in the Northeast (Pennsylvania, New York, Vermont, New Hampshire, Maine, Massachusetts, Connecticut, Rhode Island, and New Jersey).
Methodology
The 2025 Inc. Regionals ranks businesses according to percentage revenue growth over two years. To qualify, companies must meet these criteria:
- Founded and generating revenue by March 31, 2021
- U.S.-based, privately held, for-profit, and independent – not subsidiaries or divisions of other companies – as of December 31, 2023. (Since then, a number of companies on the list may have gone public or been acquired)
- Exceed the minimum revenues required for 2021 at $100,000 and for 2023 is $1 million
As always, Inc. reserves the right to decline applicants for subjective reasons.
About Inc.
Inc. is the leading media brand and playbook for the entrepreneurs and business leaders shaping our future. Through its journalism, Inc. aims to inform, educate, and elevate the profile of its community: the risk-takers, the innovators, and the ultra-driven go-getters who are creating the future of business. Inc. is published by Mansueto Ventures LLC, along with fellow leading business publication Fast Company. For more information, visit www.inc.com.

 You work with an IT service provider that learns your business, priorities, and IT needs. They work to address your needs and priorities within your budget and in alignment with your business goals and objectives. When economic conditions shift, the vendors with whom your IT service provider partners – Google, Microsoft, and others – get nervous and begin calling you directly, bypassing your trusted advisors.
You work with an IT service provider that learns your business, priorities, and IT needs. They work to address your needs and priorities within your budget and in alignment with your business goals and objectives. When economic conditions shift, the vendors with whom your IT service provider partners – Google, Microsoft, and others – get nervous and begin calling you directly, bypassing your trusted advisors.
 If you use Google Workspace or Microsoft 365, managing your services requires time and effort. Failing to do so can lead to wasted money and security risks. Here are the three most common cloud admin oversights we encounter.
If you use Google Workspace or Microsoft 365, managing your services requires time and effort. Failing to do so can lead to wasted money and security risks. Here are the three most common cloud admin oversights we encounter. Allen Falcon is the co-founder and CEO of Cumulus Global. Allen co-founded Cumulus Global in 2006 to offer small businesses enterprise-grade email security and compliance using emerging cloud solutions. He has led the company’s growth into a managed cloud service provider with over 1,000 customers throughout North America. Starting his first business at age 12, Allen is a serial entrepreneur. He has launched strategic IT consulting, software, and service companies. An advocate for small and midsize businesses, Allen served on the board of the former Smaller Business Association of New England, local economic development committees, and industry advisory boards.
Allen Falcon is the co-founder and CEO of Cumulus Global. Allen co-founded Cumulus Global in 2006 to offer small businesses enterprise-grade email security and compliance using emerging cloud solutions. He has led the company’s growth into a managed cloud service provider with over 1,000 customers throughout North America. Starting his first business at age 12, Allen is a serial entrepreneur. He has launched strategic IT consulting, software, and service companies. An advocate for small and midsize businesses, Allen served on the board of the former Smaller Business Association of New England, local economic development committees, and industry advisory boards. The current United States administration continues to issue and execute dramatic changes in US policies and programs. For businesses, tariffs and their potential impact on the economy and various business sectors gets most of the media attention. Getting less attention, US Cybersecurity Policy changes will have an immediate and potentially devastating impact on many businesses and individuals.
The current United States administration continues to issue and execute dramatic changes in US policies and programs. For businesses, tariffs and their potential impact on the economy and various business sectors gets most of the media attention. Getting less attention, US Cybersecurity Policy changes will have an immediate and potentially devastating impact on many businesses and individuals. 




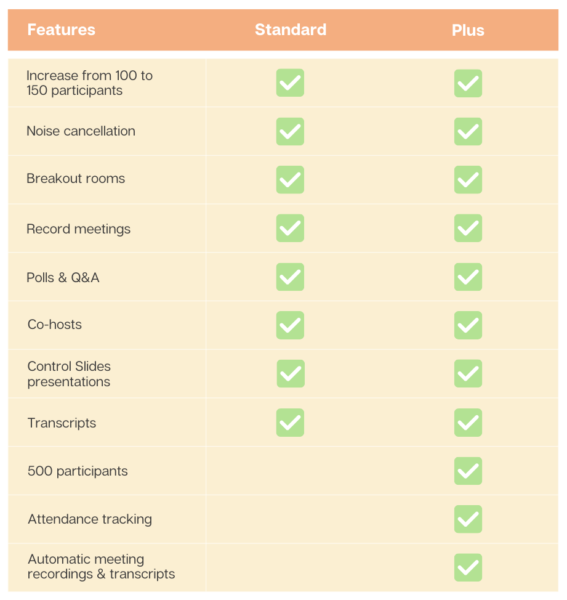
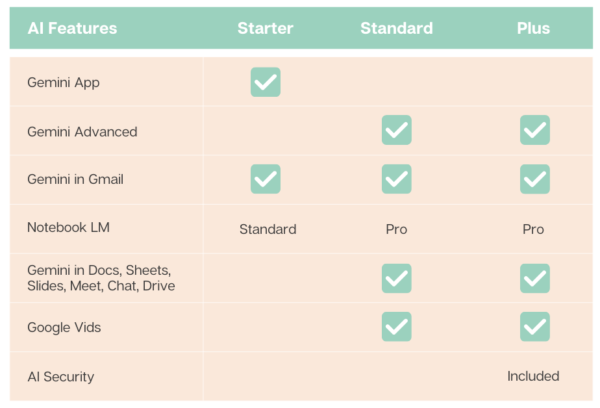
 To meet widely varying customer needs, Google offers five core subscription options spread over two tiers. For larger organizations with frontline and deskless information workers, Google offers additional, specialized license options.
To meet widely varying customer needs, Google offers five core subscription options spread over two tiers. For larger organizations with frontline and deskless information workers, Google offers additional, specialized license options.